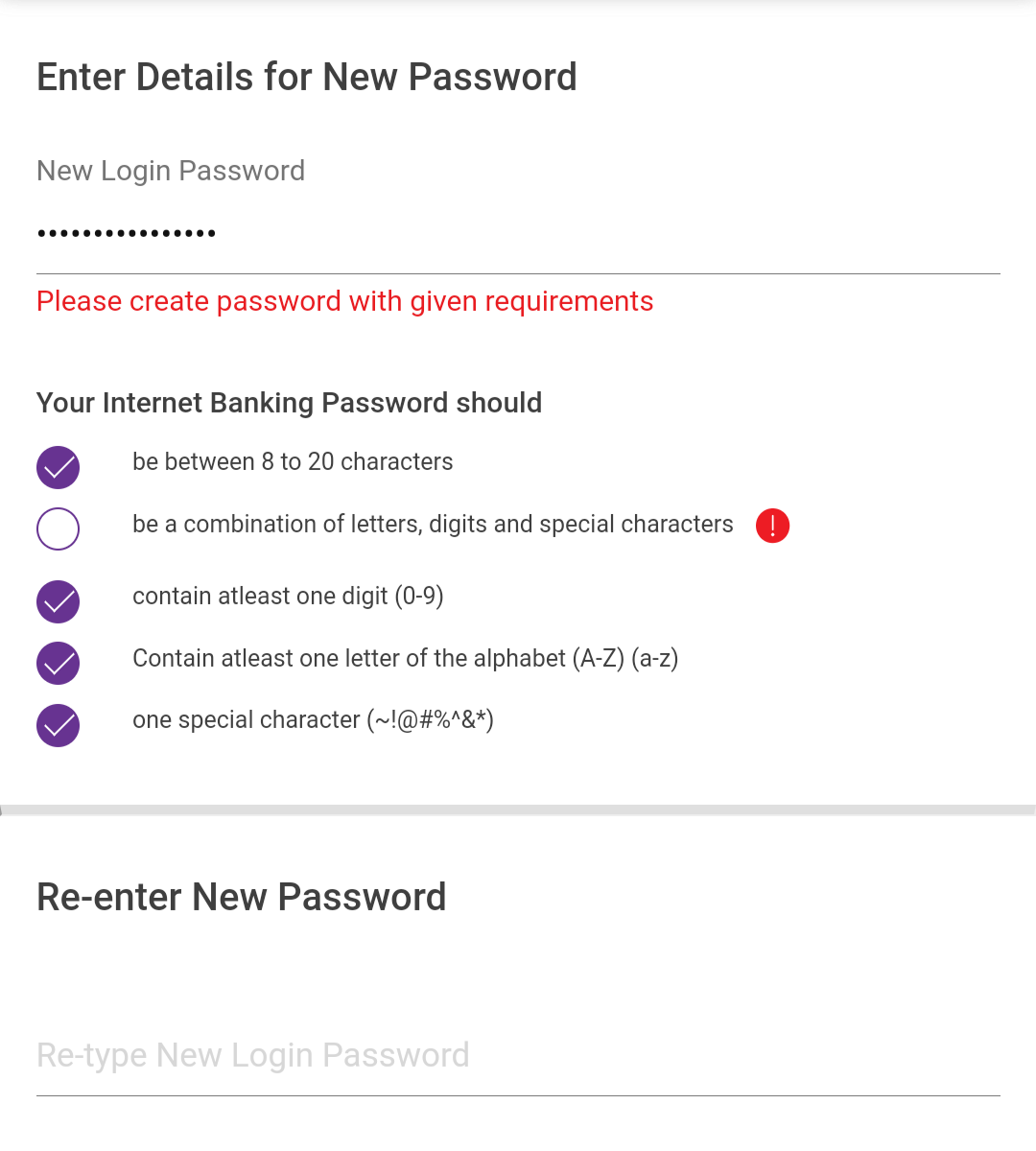
Since when is "atleast" a word?
Programmer Humor
Welcome to Programmer Humor!
This is a place where you can post jokes, memes, humor, etc. related to programming!
For sharing awful code theres also Programming Horror.
Rules
- Keep content in english
- No advertisements
- Posts must be related to programming or programmer topics
“Atleast”?
it's British. they also do "aswell"
No we don’t.
Noone should of aloud this code to go out the door. Atleast alot of other people people probably complained aswell, so your apart of a bigger group, incase you were worried.
spoiler
And yes, this was painful to type.
I miss Allie's blog alot.
Your comment is painful to read.
Your well come.
Maybe you accidentally did a permutation instead of a combination.
This was a new one for me:
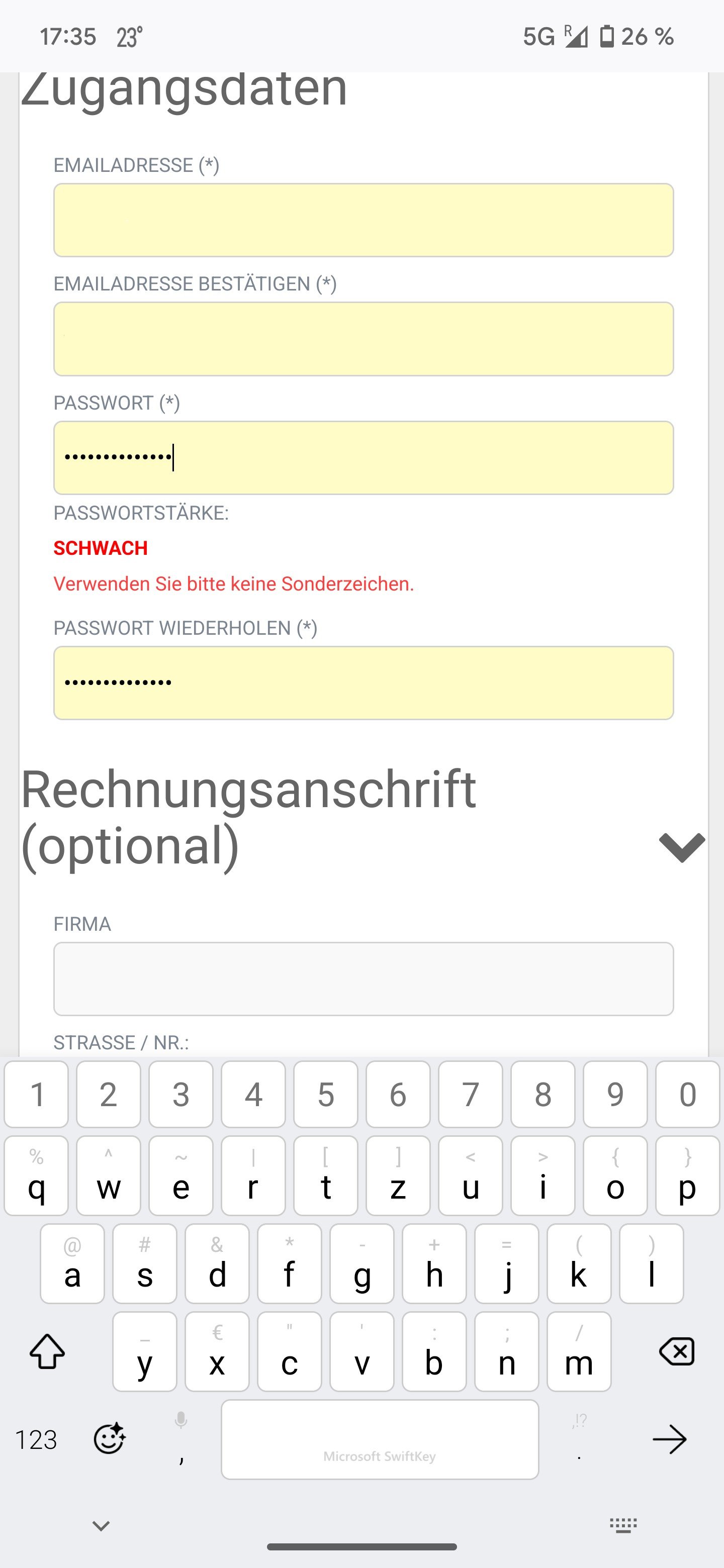
Translation: Password strength: weak. Please don't use any special characters.
It was a generated 14 char password.. (╯°□°)╯︵ ┻━┻)
The USCIS site makes it clear that your CAN use emojis in your password.
ETA: but not required.
That programmer has obviously been playing https://neal.fun/password-game/
I can never get past the geoguesser part
I got past it because it happened to throw a place from my country. And there was also a flagpole with a flag on it to really drive it home. XD
Last time I got pretty deep in, but it became impossible when the chess notation rule required Cs and Ds, making it impossible to stay below the roman numberal sum limit.
I used Google lens. Got stuck afterwards on a chess rule. The captcha rule used the notation for the chess one to complicate it further haha
I remember seeing the most optimal password for this game but now I can't find it
problem is the late stages of the game the password requirements change when your password's emojis start catching fire.
I put that out but the stupid chicken choked while I was looking for a YouTube video 4:42 long
When you enter an apostrophe, and the site returns a 500 response stating you are trying to attack it. (And yeah, it's always 500, not 400.)
I used to use a system that was perfectly happy to let you use a semicolon when setting the password, but then login would fail if you did.
Now imagine how many services just silently cut off your password at 8 characters and people never notice.
UltraVNC is very guilty of this.
Wells Fargo cuts to 14 on their sign in page but not on their change password page, ask me how I know
Once upon a time, battle.net passwords weren't case sensitive. I used upper and lower case letters in my password then one day realized I didn't hit shift for one of the caps as I hit enter out of habit, but then it still let me in instead of asking for the password again.
It was disappointing because it takes more work to remove case-sensitivity than to leave it. I can't think of any good reason to remove it. At least the character limit had a technical reason behind it: having a set size for fields means your database can be more efficient. Better to use the size of a hash and not store the password in plaintext, so it's not a good reason, but at least it's a reason.
At least the character limit had a technical reason behind it: having a set size for fields means your database can be more efficient.
If that is the actual technical reason behind it, that is a huge red flag. When you hash a password, the hash is a fixed size. The size of the original password does not matter, because it should not be stored anyway.
Correct, hence the sentence after the one you quoted :)
If any service can recover your password and send it back to you rather than just resetting it for you to set a new one, don't rely on that service for anything you want to keep secure. And certainly don't reuse a password there, though you shouldn't be reusing passwords anyways because who knows what they are and aren't storing, even if they don't offer password recovery.
Sorry, didn't want this to look like an attack or disagreement. Just wanted to highlight that point, because arbitrary maximum sizes for passwords are a pet peeve of mine.
Yeah no worries and agreed. I hate seeing commercial sites using worse password sanitization practices than I used for my first development website that wasn't even really intended for anyone else to log in to and any max length suggests the password is either stored or processed in plaintext.
IMO it should even be hashed on the client side before being sent so that it doesn't show up as plaintext in any http requests or logs. Then salted and hashed again server side before being stored (or checked for login).
IMO it should even be hashed on the client side before being sent so that it doesn’t show up as plaintext in any http requests or logs. Then salted and hashed again server side before being stored (or checked for login).
But if someone got that hashed version they could hack the client to have client side hashing code just send that hashed value to the server. You'd want to have the server to send a rotating token of some sort to use for encrypting the password on the client and then validate it on the server side that it was encrypted with the same token the server sent.
Seems complicated to me... https is probably has good enough encryption, so eh, whatever.
Yeah, if they are able to intercept traffic or access the logs, they probably already have other access to the account without needing the password. If you don't reuse passwords, then your other accounts will be safe from that.
It's possible that the passwords want through an old ass cobalt system or something that forced everything to be capitalized so to solve that they made everything non case sensitive.
But even that sounds insane as the passwords should have been hashed.
COBOL
What if they got hashed by that cobalt system :P