Now the dev doesn't need to comment this part of the code, saves him time.
Programmer Humor
Welcome to Programmer Humor!
This is a place where you can post jokes, memes, humor, etc. related to programming!
For sharing awful code theres also Programming Horror.
Rules
- Keep content in english
- No advertisements
- Posts must be related to programming or programmer topics
How’d they know it was a he
Maybe there's a specific person who keeps doing this and they wrote this error specifically for him.
Come on Dave sort yourself out.
You know this is a porn site then! 😂
At my job, we have an error code that is similar to this. On the frontend, it's just like error 123.
But in our internal error logs, it's because the user submitted their credit card, didnt fully confirm, press back, removed all the items out of their cart, removed their credit card, then found their way back to the submit button through the browser history and attempted to submit without a card or a cart. Nothing would submit and no error was shown, but it was UI error.
It's super convoluted. And we absolutely wanted to shoot the tester who gave us this use case.
This makes want to become a tester. It scratches my evil itch just the way I like it.
If that broke the software it sounds like you have a very good tester.
And we absolutely wanted to shoot the tester who gave us this use case.
Why? Because he tested well and broke the software? A user changing their mind during a guided activity absolutely is a valid use case.
I think they meant shoot in like a friendly way. You know, happiness bullets!
Like how I always say to my friends, "Look at me again and I will fucking murder you and rape your family dog".. it's just in good fun.
Oh, THAT's what "friendly fire" means!
hey that tickles!
Better the tester than a user.
Whats the difference?
As of now, I consider you an enemy
Brand reputation?
Being prepared for the eventuality, knowing the consequences and deciding what to do about it before it happens for a user.
Different mindset. A user doesn't want to find bugs but get shit done.
I might be the one hitting that link just to see what happens.
"Let's see how good their testers are."
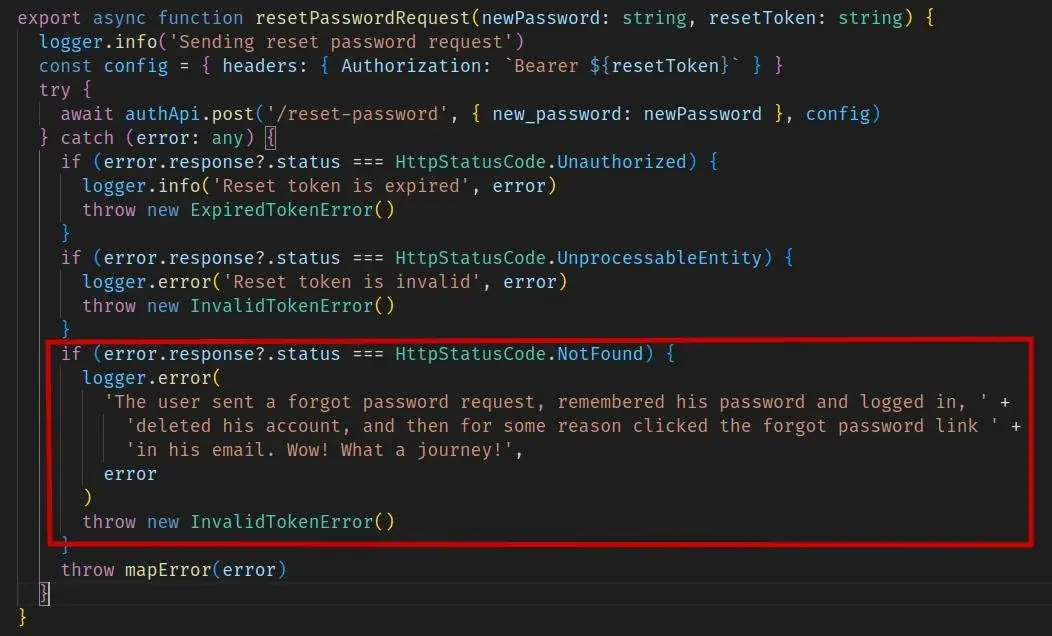
Hoh man what a journey. And I love that this incredibly complex situation is the only reason that status would return. What a fun time debugging that would have been
Not really the only reason. It would be better to just return "token invalid".
It could occur by someone messing with the URL from the reset password email, like accidently adding an extra character before pressing enter
Or a poor email client that wraps the URL and doesn't send the complete one when clicked.
Or someone attempting to find a weakness in the reset password system and sending junk as the token.
Or an email client where you double click the link text to select it and press copy, and somehow this puts the link plus a trailing space in the clipboard to be pasted into a browser.
The type of error where you have to give up trying to understand the user.
It's quite simple actually: The user wanted to delete their account, but forgot their password so they requested a password reset. Before the password reset email was delivered, the user remembered their password and deleted their account. The password reset email is finally delivered and apparently some email clients open all the links in the background for whatever reason, so it wasn't actually the user who clicked the password reset link.
apparently some email clients open all the links in the background for whatever reason
What? Really??
Yes, e.g. outlook replaces links in mails so they can scan the site first. Also some virusscanners offer nail protection, checking the site that's linked to first, before allowing the mail to end up in the user's mail client.
Thats why you never take actions on a GET request, but require a form with button for the user to do a POST.
Yep. Apparently outlook does this and afaik because some kind of link sniffing/scam detection/whatever, but it does it by changing the first characters of each query argument around.
We spent amazingly long time figuring that one out. "Who the hell has gotten Microsoft service querying our app with malformed query args and why"