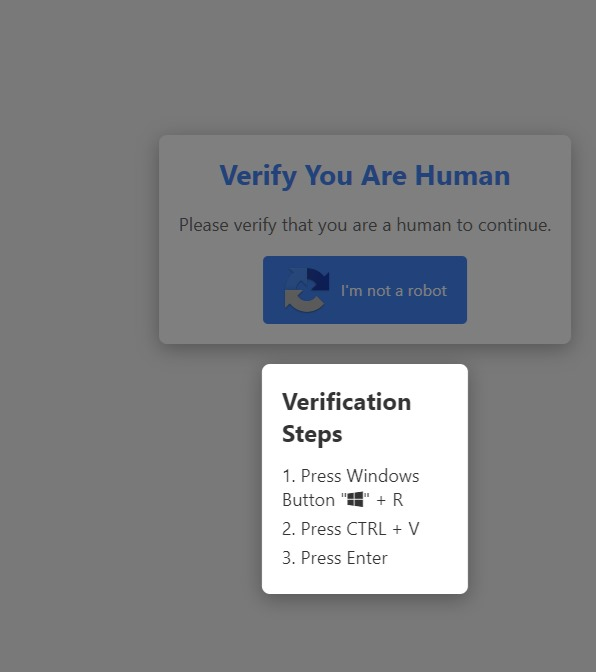
This is actually pretty smart because it switches the context of the action. Most intermediate users avoid clicking random executables by instinct but this is different enough that it doesn't immediately trigger that association and response.
Technology
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related content.
- Be excellent to each another!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, to ask if your bot can be added please contact us.
- Check for duplicates before posting, duplicates may be removed
Approved Bots
Just reported by Mohamed Aruham on Twitter
The oldest tweets I could find that actually started reporting this are from ~16 days ago.
https://x.com/Piotrdotcom/status/1829126494574067992
They reference a page here that was posted on Aug 29th.
So inventive these guys. If only we could harness that ingenuity for the common good instead, it would have a huge impact.
Fwiw there are a large number of people who volunteer their time and effort toward worthwhile projects. It's just they don't get rewarded anywhere near the level of benefit that they provide.
That’s going to catch some people, especially older ones.
Yet if I was helping my elders over the phone, I'd get all sorts of "What Windows key?", "I can't find that Control key", or "I did that key, the plus key, and then my hand slipped and I minimized everything."
General rule of thumb for me to interact with a website and read or watch whatever I want .... if you require me to do more than two things to show me the content I came to see, I'm closing the tab or windows and moving on.
If it's really important and security related, I'll take my time and carefully examine everything I do.
Otherwise I'm not clicking more than twice and definitely not using my keyboard to see your dumb website or TikTok video.
Failed to execute child process: "calc.exe" (No such file or directory).. hehe
Wouldn't it require elevation?
Yet another example of why running as root/admin is a Bad Idea©
That should be easy on windows, but user permissions might also be enough for whatever it does.
Once you run something on windows, elevation is just a thing of using the right toolbox.
No, why would it? It will run code in the context of the current user which is absolutely enough to start a new process that will run in the background, download more code from a attacker server and allow remote access. The attacker will only have as much permissions as the user executing the code but that is enough to steal their files, run a keyloggers, steal their sessions for other websites etc.
They can try to escalate to the admin user, but when targeting private victims, all the data that is worth stealing is available to the user and does not require admin privs.
Exactly. The moment you hit Enter, the computer becomes part of a botnet on every login.
Yes. The prompt asking you if you wanted to do it or not would come up next. Unless they figured out some sneaky way to do something to avoid using admin.
90% of users when they are presented with the UAC popup when they do something:
"Yes yes whateverrr"
Deploy a user-level payload that is auto started on login. The computer is now part of the botnet and can already be used for useful ops. Deploy a privilege escalation payload later if needed.
It seemed odd to me that a Web site could write to or read from the clipboard without the user approving it. That would be a pretty obvious security and privacy issue. From what I gather, on Chrome sites can write to the clipboard without approval, but they need approval to read. ~~On Firefox and others any access requires permission. Thus this exploit seems limited to Chrome users.~~
@SkaveRat pointed out that it doesn't require permission, only interaction. So likely there's a button that's clicked that writes to the clipboard, and most browsers are susceptible to this.
not when there was a user intent like clicking a button.
For example in this screenshot, it's likely that there's only the "verify I'm human" button first, you click it, the steps pop up, and at the same time the command ist copied into your clipboard
Exactly, copy requires a click but there's no rule that the copy button has to look like anything particular
That's a sneaky one.