this post was submitted on 14 Sep 2024
1631 points (99.1% liked)
Technology
59405 readers
2941 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related content.
- Be excellent to each another!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, to ask if your bot can be added please contact us.
- Check for duplicates before posting, duplicates may be removed
Approved Bots
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
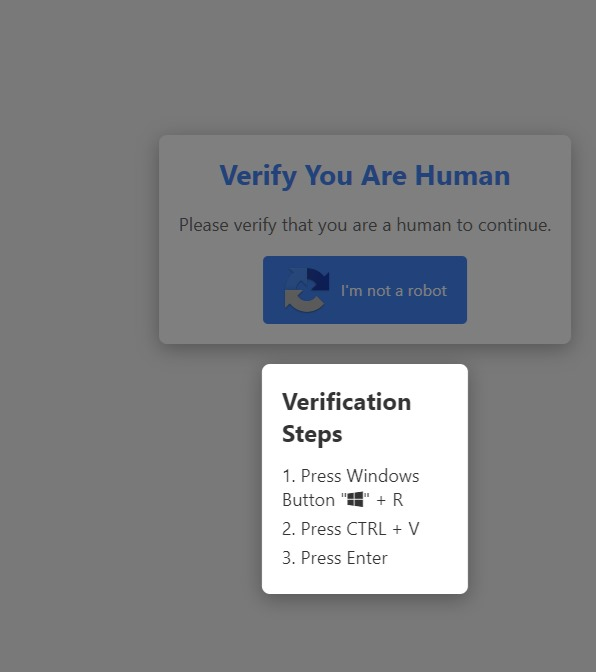
Wouldn't it require elevation?
Yet another example of why running as root/admin is a Bad Idea©
That should be easy on windows, but user permissions might also be enough for whatever it does.
Once you run something on windows, elevation is just a thing of using the right toolbox.
No, why would it? It will run code in the context of the current user which is absolutely enough to start a new process that will run in the background, download more code from a attacker server and allow remote access. The attacker will only have as much permissions as the user executing the code but that is enough to steal their files, run a keyloggers, steal their sessions for other websites etc.
They can try to escalate to the admin user, but when targeting private victims, all the data that is worth stealing is available to the user and does not require admin privs.
This here. The most important thing on your computer are all your session cookies, which are, well, accessible with permissions your user account already has.
Dudes don't care about making your shit into a botnet, or putting a rootkit in your firmware, or whatever other technically complex thing you care to think about: they're there to steal your shit, and the most valuable shit you have is sitting there out in the open for the taking for anyone who makes it past a very very low bar of 'make the user do something stupid'.
Exactly. The moment you hit Enter, the computer becomes part of a botnet on every login.
Yes. The prompt asking you if you wanted to do it or not would come up next. Unless they figured out some sneaky way to do something to avoid using admin.
90% of users when they are presented with the UAC popup when they do something:
"Yes yes whateverrr"
🤷♂️ people are going to take the path of least resistance
It would be trivial to add a "please click 'yes' to the UAC prompt to allow verification" screen, so that isn't really going to stop anyone.
I've seen a bit of office malware in the past that did that, where it had a bunch of images instructing you to enable macros and that.
Deploy a user-level payload that is auto started on login. The computer is now part of the botnet and can already be used for useful ops. Deploy a privilege escalation payload later if needed.