Yes. They deserve nothing. LIE.
People Twitter
People tweeting stuff. We allow tweets from anyone.
RULES:
- Mark NSFW content.
- No doxxing people.
- Must be a pic of the tweet or similar. No direct links to the tweet.
- No bullying or international politcs
- Be excellent to each other.
- Provide an archived link to the tweet (or similar) being shown if it's a major figure or a politician.
I'm often [email protected] with a name of admin admin, a birth date of 01/01/1970 a phone number of 4041234567 and address of 123 main street anytown, USA
And then if they expect me to retrieve info from said email or phone number I simply move on
You can save different identities using one password and then every time you sit down at your computer you can just make up new details for those identities in one password so that when you go to the mall, You're not always Chungus McGrungledunk, but sometimes they're going to be offering a free trial to, Faurtstick Blastschish or whatever name I give the email address I spin up for the purpose.
It's good to register a burner domain that you don't care about and once you have the processed enough different identities through it simply stop renewing it and sign up for new one.
Breathing isnt free in todays world
That's when I use the oldest human invention: LYING.
Fake email, fake address, tell them I make more than the highest option they give for the income, make up the entirely unique gender of squorp, etc.
On some public networks, my Wireguard VPN just doesn't work. Although I can connect to my server using SSH, so I assume the network was configured to block certain ports or how else can it block VPN connections?
Many networks block UDP ports, which is what wireguard uses. If you can configure the serverside part of the VPN, you could try running it on port 123, which is used for the network time protocol (ntp), which also uses UDP and is open nearly everywhere
having no idea what the fuck these letters mean I think this dude is correct
I went to a restaurant recently that asked me to pay my bill with the QR code on the tablet. Scanned it, and the first thing it did was ask for my phone number to verify my "account" by sending me a code.
The server didn't understand that I wasn't going to do that, and they needed to run my credit card like normal or I wasn't paying.
Oh, it's not a swindle. What you do is, see, you give 'em all your credit card numbers, and if one of them is lucky, they'll send you a prize!
i have an alter ego called Nunya Business
email: [email protected]
he uses a VPN when connected to public wifi
Rule of thumb on the Internet, if you can't see how it's payed for (subscriptions, ads, donations...) then you probably pay with your personal data.
Especially true for apps and games. "Play totally free, no annoying adds or in-app purchases" means "Here is a trojan horse pretending to be a game while farming every possible information from your device to sell to the highest bidder".
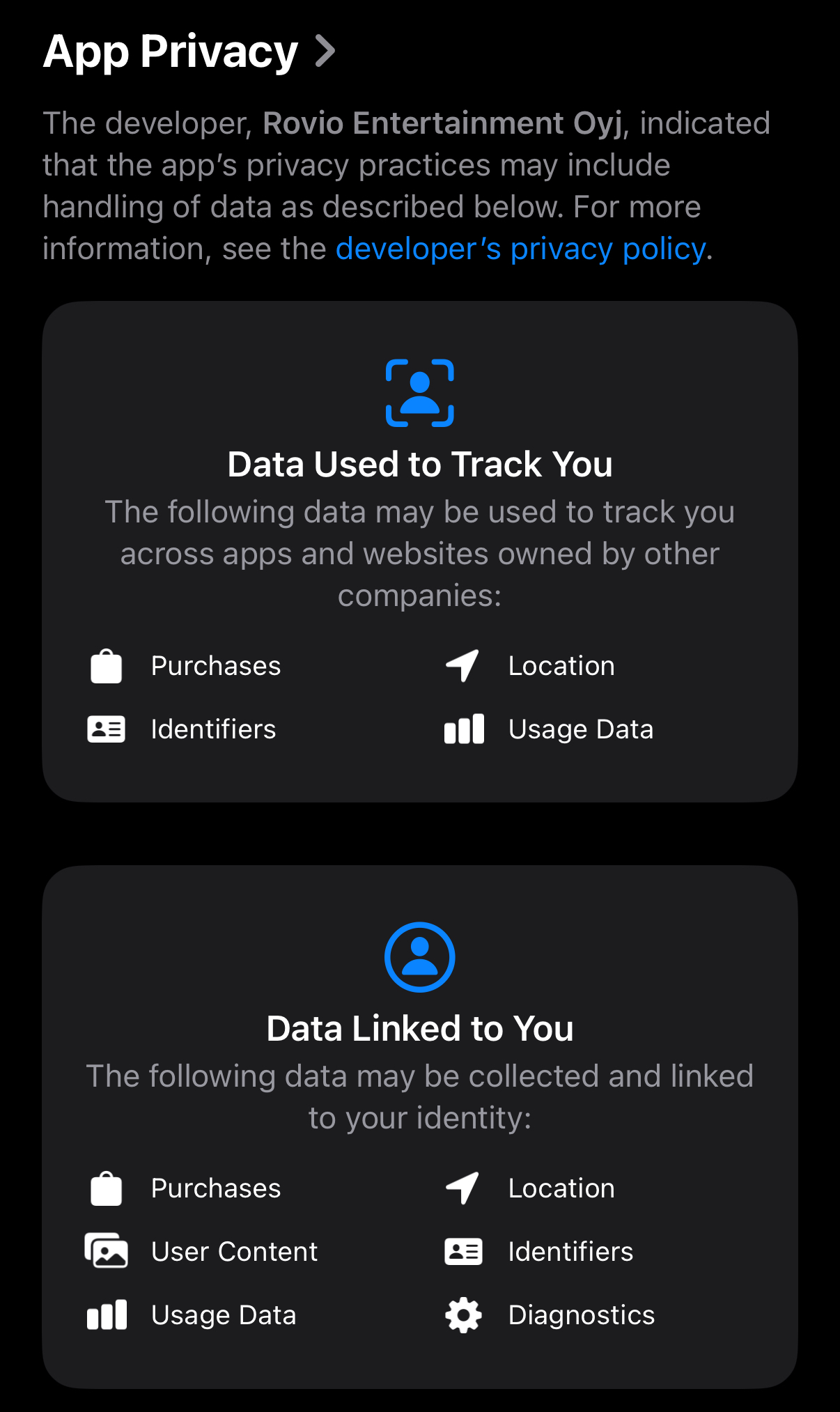
Small shout out to Apple here, perhaps, for their little privacy report card. Here is Angry Birds 2:
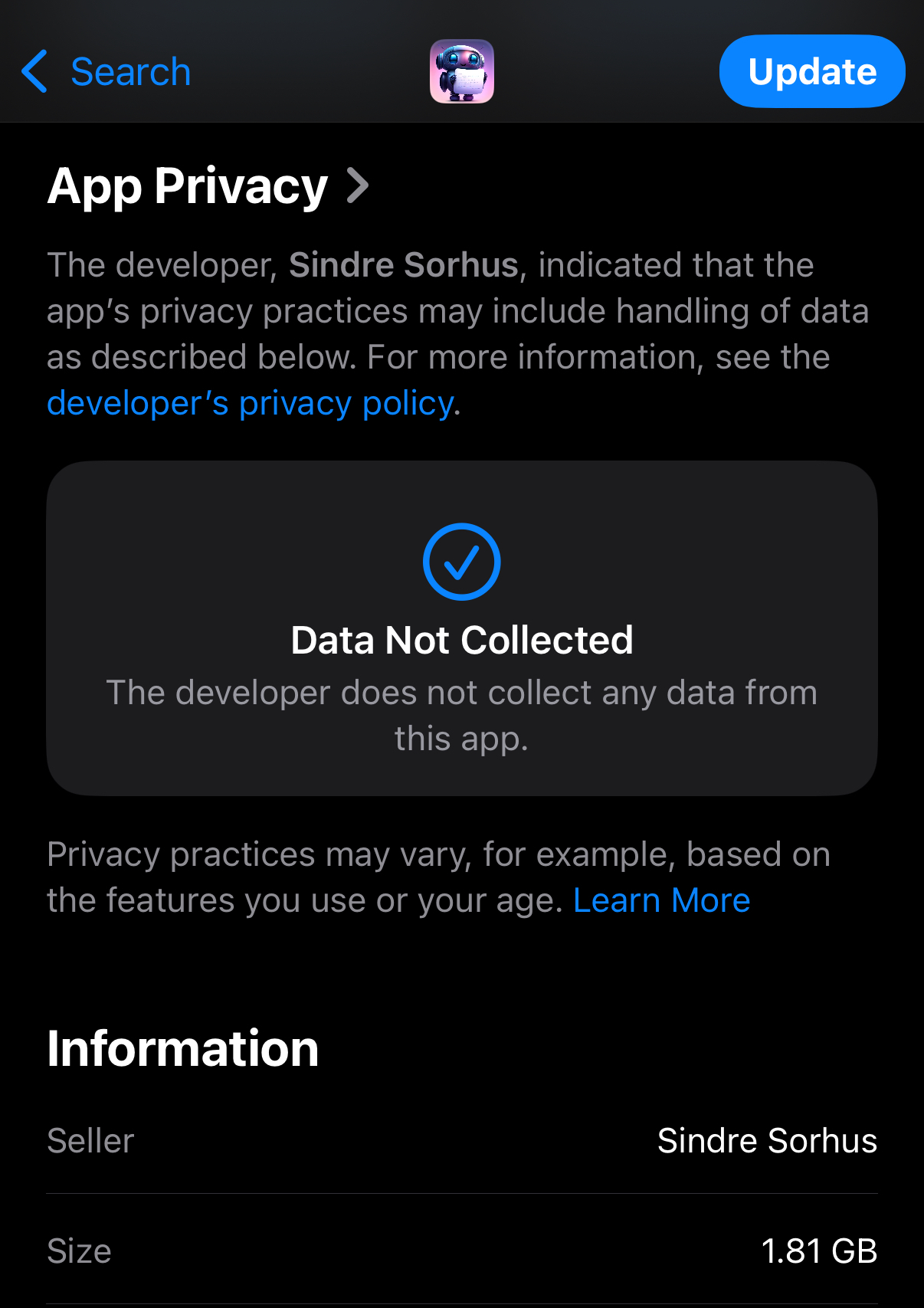
A transcription app by a cool solo dev:
Y'all trust these?
Fake info, then VPN.
Walmart does similar now, though they don't ask all that much. The bogus account I set up is...
Email: [email protected]
Password: Walmart1
Name: Anonymous Human
Enjoy your anonymous free WiFi at Walmart haha!
I like [email protected], same for first/last name. Only problem is I'm not the only one so sometimes it's already taken.
My email is whatever shit protonpass comes up with when I generate a random alias. Phone number is 3334445566 Name is: lol no Gender is undisclosed DoB is January 1st of the first year I can select. Otherwise, 1900 And income is 1.
There, free WiFi.
I usually use:
Email - [email protected]
Name - Nah Nope
Gender - prefer not to say
DoB - same as you
Phone - just random digits, or if I'm feeling spicy the phone number of a guy I used to be buddies with who fucked me over
Income - never been asked for this yet, probably go with something outlandish....like 1
That said...A wifi access point that requests that info is almost certainly not private for every other trackable thing you do with that wifi, however.
If it's an open WiFi (no WPA password) packets are not encrypted anyway, so anyone on this AP can easily see everything that comes through it. A decade ago, when most websites allowed plain HTTP, there was a Firefox extension which let you hijack the Facebook or Twitter session of anyone connected to an open WiFi with a couple of clicks.
Nowadays everything is hopefully encrypted at the application level, so while attackers can see where the data goes, they can't actually read it.
It's good practice to assume that this is true of every network you don't control.
What would stop you from using random, invented data?
Don't use random, invented data. That's wrong. Use the real data of a ceo or other executive from a company that spammed you. Or if you have the time find out who owns the mall and use their information.
Even better. Though it takes some work to gather that data.
But... that requires the internet to research
That's so evil and so amazing
Sounds more like justice from down here.
You wouldn't just go on the internet and lie would you?
No but lie and then go on the internet, that’s a different story

