The same thing happens with webkit.
Firefox
A place to discuss the news and latest developments on the open-source browser Firefox
Please don't post pictures of text without transcribing the words

Sorry I'm blind, and I cannot see the image. Would you mind telling me what you posted?
A gif
the title describes the screenshot entirely
Fuck blind people who need to google error messages, right?
/s
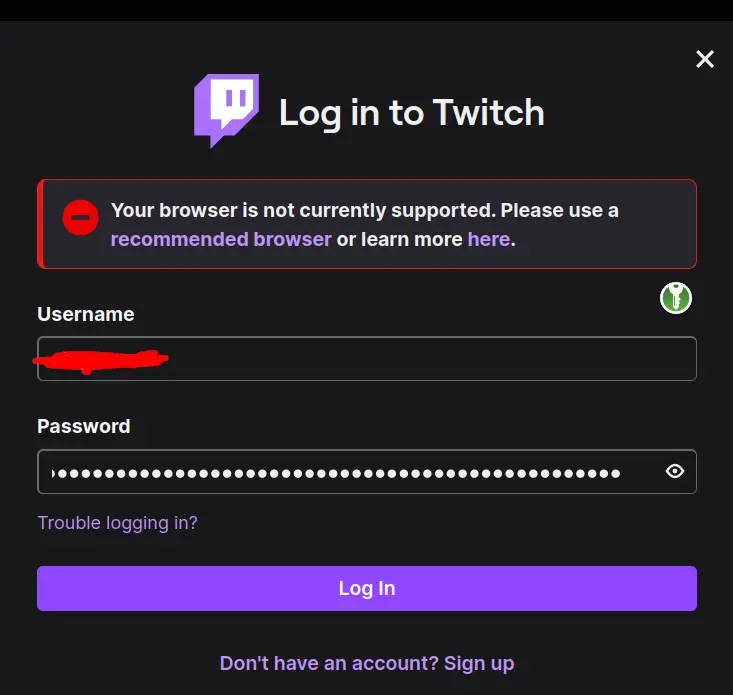
Upper screen: [Twitch Logo] Login to Twitch
Box with error notice: Your browser is currently not supported. Please use a recommended browser or learn more here.
Then there is just a standard login form
Just a comment: IMO it's not worth using strong passwords on which you depend on privative/unknown security platforms. Who knows how many times they get hacked or have backdoors? Unless they specify they only store the hash I refuse to sacrifice one of my strong passwords.
Edit: To all talking about password managers. I don't believe in single point of failure as a way to go. The fact that i've to explain that xd...
Bro over here still using one of his "strong passwords" trying to give other people security advice 😅
Genuinely terrible advice. Every popularly available password manager service hashes all your passwords, if they have a data breach they have extremely strict reporting compliance and the majority of services will re-hash all your passwords. If youre so extremely concerned about that, host your own.
But what concerns me the most is
Unless they specify they only store the hash I refuse to sacrifice one of my strong passwords.
... What to you mean sacrifice?
Keeping all on one password (password manager) is a single point of failure, which i don't like. I mean sacrifice because my brain can only remeber a few 512bytes long passwords (again i don't use password managers because of single point of failure).
Isn't your computer a single point of failure? A keylogger will get your password database or you manually entered passwords all the same.
Who says I have the same password for my root, my user account, and my LUKS encrypted hard drive? Losing one doesn't mean losing everything like in a Password manager.
Not that, I meant a keyloggers could get the password to your password database in the same way it could get any accounts you log into by typing your password into a browser.
Does your threat model involve The Mossad? There's no way on earth that you are genuinely remembering multiple 512 byte random passwords, let alone actually taking the time to type them in.
Having a password manager, with MFA, a strong master password, and rule based device verification is ultimately more secure as you can have every password be randomized.
Best practices are best practices for a reason. I recommend you follow them.
Mossad or other agencies arent God. If my device is cryptographically secure and doesn't have backdoors it's unfeasible to access any data with current technology. I guess you are right if you take into account Intel management engine and similar, but since I use libreboot bios that does not apply to my computer (only place that I treat as secure).
If you use Apple, Microsoft, google, etc devices, those are 100% vulnerable even if you use idk rsa 2048 (xd). The problem is who you are trusting.
That's a good point. But, yeah again I don't fall in those categories. I try to ensure that my security is only based and covered behind cryptography theory and nothing else.
The point is that if someone really wants to get into your device, they will. It doesn't matter if youre using open source firmware, in a custom implementation of linux, on a MIPS CPU, and you personally build every package from source and complete a compliance code review before installing it, etc.etc.etc. If government agency x is targeting you specifically, your best line of security is to lock your device in a safe, take a boat into the middle of the ocean, and then dump it at an unrecorded location and never retrieve it.
A device is only secure as long as you are not using it, and it is not accessible physically, or by network.
You do you dude, I'm just saying your advice is awful for the average user.
You should use randomly generated passwords from a password manager, there is no short supply of strong random passwords.
Waste one of my 2272657884496751345355241563627544170162852933518655225856 possible 32 character passwords on Twitch! Outrageous! What if I run out?
Sacrifice? Tf you on about?
That is definitely an autofilled one-off password from a password manager.
You need to disable resist fingerprinting. It's annoying, but you can reenable it after you've logged in
No, you need to email twitch that they have a bug.
And boycott them if they're intentionally trying to harm marginalized folks.
I'm all for FOSS browsers, but how are Firefox users marginalized folks?
The issue isn't Firefox. The issue is users who have privacy protections enabled. Marginalized folks need such protections to stay safe
That's the solution if you immediately tried to login and it didn't work.
Twitch login has in general very misleading error messages. The exact same message with unsupported browser also appears if you take too long to login
Firefox is actually one of the recommended browsers, if you were to click on that link. Twitch just has some issues sometimes
Yup, I use Twitch all the time on Firefox (including yesterday), and with an ad-blocker as well.
Stop using recommended when you mean required FFS.
I had this come up when I was using a locked down version of FF.
Basically what happened was the security settings were not allowing Twitch the access it required.
Once I went through and allowed access it worked fine.
That is trending Firefox users find a site rejecting the browser 🤔
Seems to be working OK for me on FF with Ublock and Privacy Badger running.
Differing experiences might mean that Twitch is performing A/B testing on blocking Firefox.
Usually it means that OP either uses a "hardened" fork, or did some messing around with about:config like resistFingerprinting, without understanding the ramnifications of such hardening on various web technologies that aren't primarily related to tracking/tracing.
Now that is a long password lol
Idk someone could probably brute force it in only a few trillion years, I'd make it longer if you plan to be using Twitch long-term.
You assume the person would never change the password. Someone with that long password is probably security concerned and is likely to change it after some time, even if its once in a year.
NIST does not recommend changing passwords. Its usually a bad practice
Why is changing passwords bad practice? What is the reasoning behind this? Changing passwords is highly recommended. There are many reasons why one should do this. Found this article: https://www.linkedin.com/pulse/why-passwords-must-periodically-changed-roger-grimes and don't agree. The argumentation seems like if you have to remember all passwords, but totally ignores password managers.
NIST used to tell orgs to require password rotation. Some years ago they changed their recommendation with an explanation that it adds not security benefits while it encourages users to write down or use shittier passwords.