this post was submitted on 20 Oct 2024
428 points (98.9% liked)
Piracy: ꜱᴀɪʟ ᴛʜᴇ ʜɪɢʜ ꜱᴇᴀꜱ
54716 readers
222 users here now
⚓ Dedicated to the discussion of digital piracy, including ethical problems and legal advancements.
Rules • Full Version
1. Posts must be related to the discussion of digital piracy
2. Don't request invites, trade, sell, or self-promote
3. Don't request or link to specific pirated titles, including DMs
4. Don't submit low-quality posts, be entitled, or harass others
Loot, Pillage, & Plunder
📜 c/Piracy Wiki (Community Edition):
💰 Please help cover server costs.
 |
 |
|---|---|
| Ko-fi | Liberapay |
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments

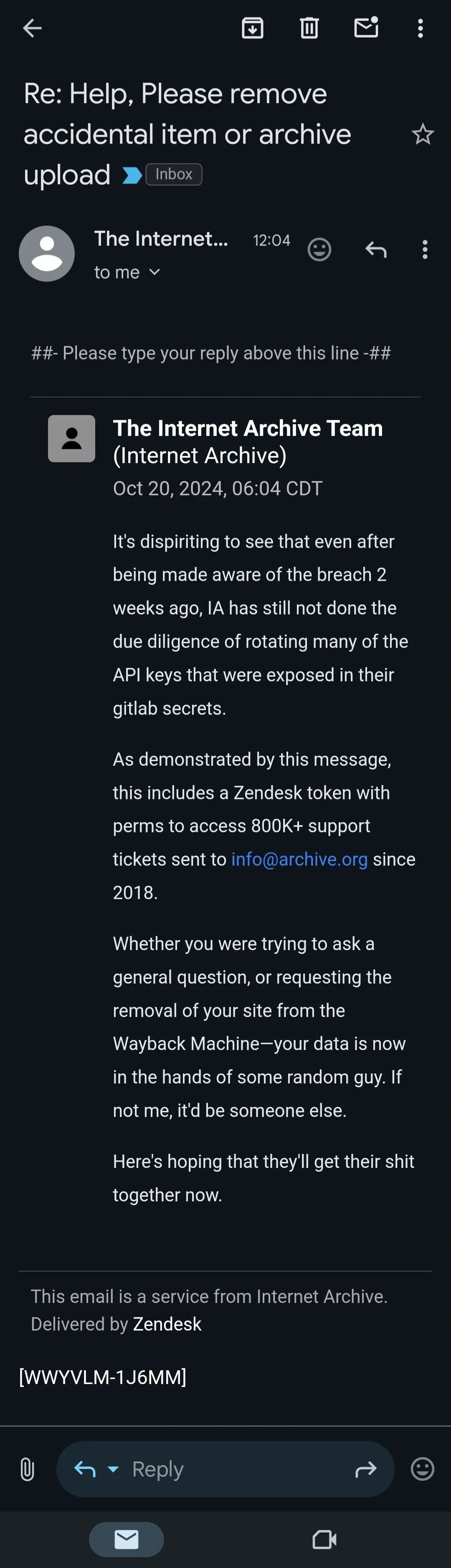
If they were really "the hero", they'd follow the bare minimum of responsible disclosure best practices, and allow 90 days between privately alerting them of the issue and going public with it. Two weeks is absurd.
90 days to cycle private tokens/keys?
90 days is just the standard timeframe for responsible disclosure. And normally that's just a baseline with additional time being given if there's genuine communication going on and signs they're addressing the problem.
90 days is standard for "you're code is fucked when someone presses this..."; if the issue is Dave left the keys in the parking lot and someone copied them, two weeks is more than enough time for them to recieve the notice, create a ticket to rotate the keys and a ticket to trigger an investigation (gotta document anytime an org fucks up so it doesn't happen again, right?). Maybe I'm over simplifying it though, I don't know how their org operates.
I agree in general, but
This is exactly why just sticking to the 90 day standard is better. For the supposed security researcher it's a CYA move at worst.