Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
view the rest of the comments
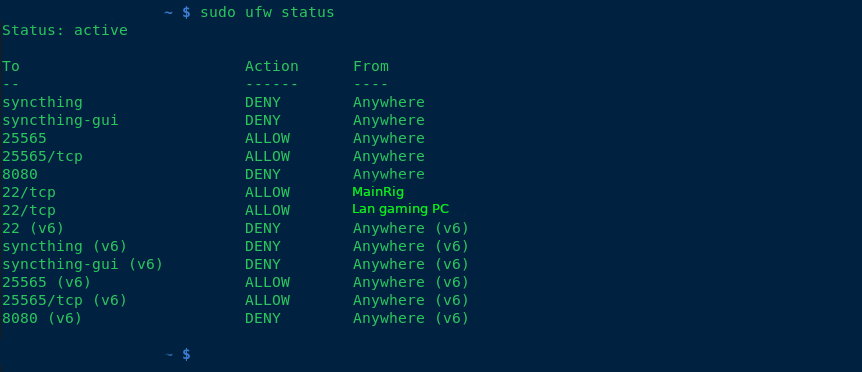
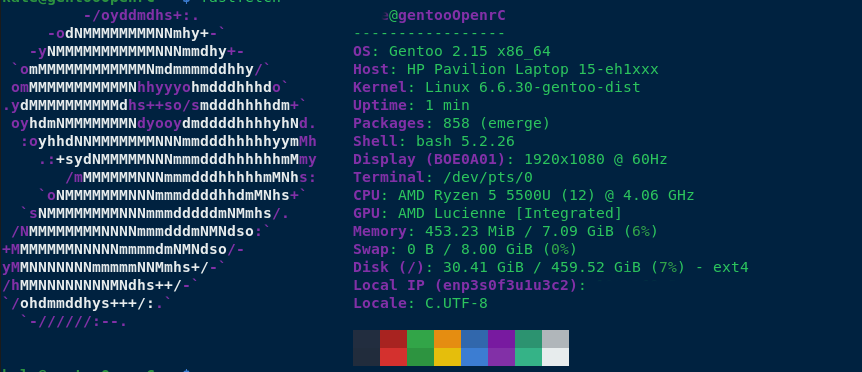
Is this machine sitting in your LAN, or on its own firewalled off network with a DMZ? No matter how secure it is, you don't want it on the same network as the machine you do your taxes on.
A good poor mans option is to get a pfsense box with 3 NIC's. One for WAN, one for LAN, and one for the machine you publicly host with.
Setup firewall rules so that LAN can reach the MC host on needed ports, but not the other way around.
Currently the plan is to use my 48 port cisco switch and put the server on a separate vlan. I assume that is very similar to your pfsense solution? Please correct me if im wrong
You're adding attack surface by keeping them separated only by vlan. VLAN hopping exploits exist, especially in older firmware, ESPECIALLY on EoL units.
Pfsense is a proper router/firewall built on one of the most hardened networking stacks on the planet. Plus it catches regular software updates, no matter how old your hardware is. You can run it on an old PC with a cheap quad gigabit nic card from eBay if you'd like.
If I might ask, what do you have handling your inter-vlan routing/firewall? Is it the same box you use to handle the firewall/routing between your WAN and LAN?
also follow up question, alot of people are saying to make the mine-craft server run in a vm for host isolation. So what if i spun up 2vm's
#1 would be a virtualized instance of pf sense, i would then have ethernet 1 on dogtown give internet to the base gentoo install, then have a Ethernet 2 go into PF sense, which will then have firewall rules to restrict access to the vm minecraft server. would that work? or is there somthing im misisng?
Diagram added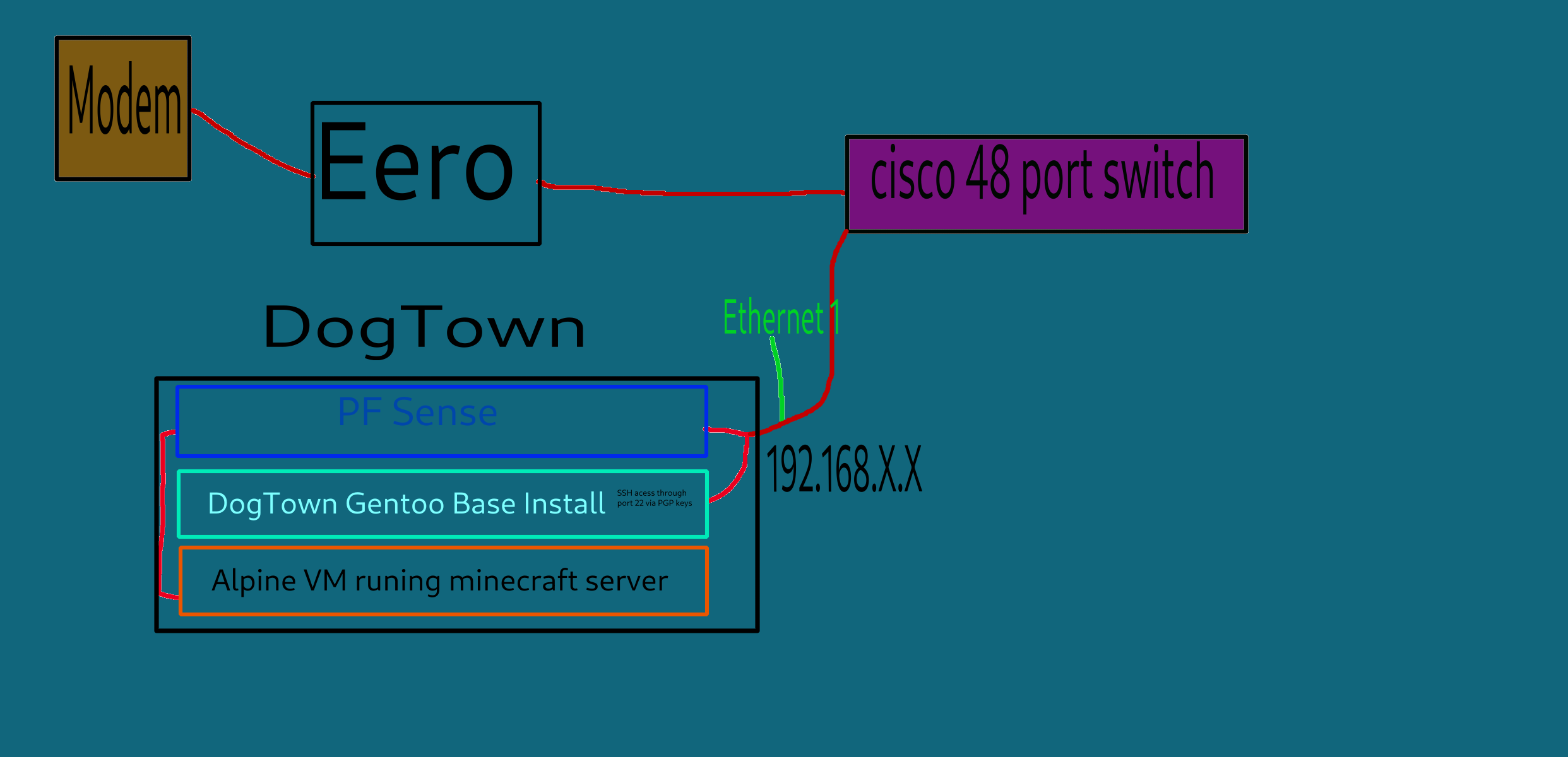
currently my setup is a dsl modem that goes, to my router/WAP which is a eero, that i plan to eventually replace with a Banna pi R4 which will run openwrt. but as of now the eero goes to my 48 port in my server room, and i have all my computer jacked into that. so to answer your question, my firewall is handled by my router and individual local rules by my machines. im kinda new to self hosting and port forwarding and pfsense looks pretty useful. i know pfsense is based on freebsd so is that a big plus vs openwrt?
please let me know, what some potential solutions could be.
Pfsense is a lot more feature rich than openWRT, especially when it comes to firewall features. Personally I just use openwrt to run my access points.
I would replace that eero unit with an old dell optiplex with pfsense, and forego trying to virtualize PFSense.
Not sure what hardware is in that eero, but if you wanted to keep it as just a basic AP, that isn't a bad plan.
After that get a second optiplex for publicly hosted stuff. Keep that on a separate port on your PFSense machine, completely firewalled off from the rest of your network via pfsense, only allowing traffic from LAN to your server.
Physically separating your internal network, and publicly hosted services, as much as possible is the goal.
If you can only afford one new piece of hardware, I'd get the pfsense box, and set it up as a wireguard VPN server, disabling the direct port forwards to the VM running Minecraft. Though your friends would need to install a VPN client, and youd have to provide config files.
A used optiplex on eBay usually isn't much more money to get up and running than most Linux SoC's after all the adapters and kit is purchased, and they're usually specced out way better.
Actually if you wanted to do physical DMZ separation, and wireguard you'd really be doing good, but that's probably a little paranoid.