As a non programmer, is the joke that humans will retype their password assuming that they made a typo?
If so, sick indeed.
As a non programmer, is the joke that humans will retype their password assuming that they made a typo?
If so, sick indeed.
took me a solid 30 seconds of re-reading to get the joke
It's not quite complete without code on the password reset page to tell you that you can't reuse your password.
This could actually work though lol, it's genius
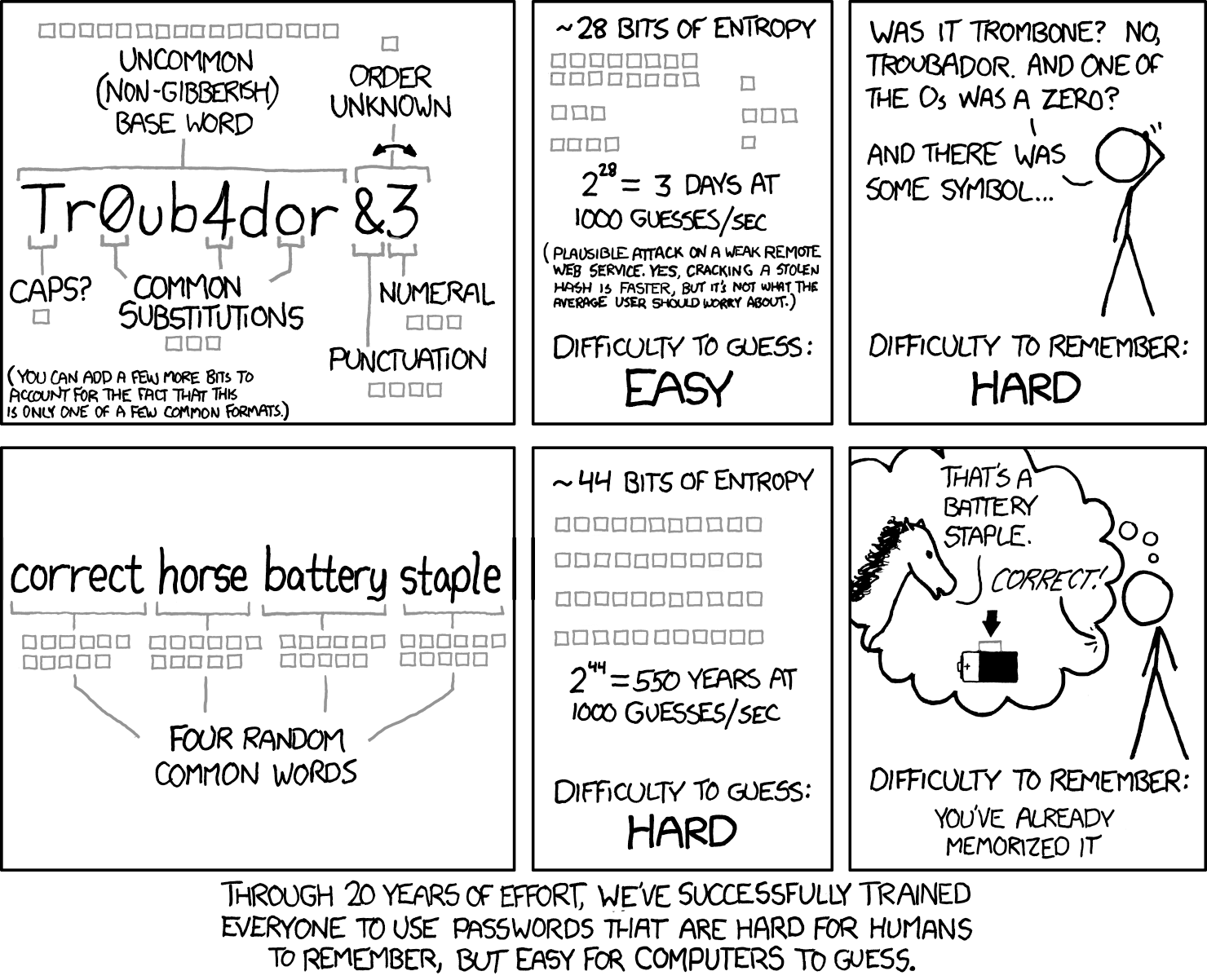
Rainbow tables and presumably newer stuff I haven't heard of make this sort of thing weaker than it used to be
The rainbow table would have to include every four word combination. At around half a million words in the English dictionary, that's not a small number.
As another XKCD comic illustrates, it's cheaper to use a wrench.
Dictionary attacks have been around for a long time, but It's still quite strong especially if you throw in a number.
A fully random 8 character password has about 10^14 brute force combinations (assuming upper and lower case + the normal special characters). 4 words choosen at random from the top 3000 words (which is a very small vocabulary really) is 10^13 dictionary attack combinations, add a single number or account for variations in word style (I.e maybe don't always use camel case) and you've matched the difficulty. If you use 5 words it's 10^17 combinations.
A password manager and a hard password is a better idea but there are cases where you can't use a password manager (like the password to said manager).
Salting makes rainbow tables pretty much useless, and salting has been a standard practise for a few decades now.
Yeah I thought about adding a note that it's pretty outdated - and dictionary based scans were always possible even if less common in the old days - like those infamous passwords "God", "Love", "secret", or like "admin".
The artist is pretty smart most of the time though so I presume they were aware of that possibility and meant that on a more basic level there are multiple ways to make passwords easier for a user to remember, not necessarily just this one rather simplistic take but as part of a whole approach. Then again, they didn't say that, and instead said this, thus the controversy.
Personally I gave up entirely and now I don't even know what any of my own passwords are, though my password manager does:-). I guess... if you cannot beat them, join them!?:-P
How does a rainbow table help here? They're more for decoding unsalted encrypted database tables, rather than for actually trying to login.